Digital Identity + Customer Experience: Updating the DBN’s Digital Identity Dataset
As student analysts with the Digital Benefits Network (DBN), this summer we worked on updating the DBN’s landscape research on digital identity in public benefits applications. First published in May 2023, this project examines when and how online public benefits applications require applicants to create accounts and take other steps to verify their identity. The project includes data on more than 150 online applications from all states and territories for:
- Supplemental Nutrition Assistance Program (SNAP);
- Temporary Assistance for Needy Families (TANF);
- Medicaid;
- Special Supplemental Nutrition Program for Women, Infants, and Children (WIC);
- Child Care Assistance (CCAP); and
- Unemployment Insurance (UI).
How state agencies structure online account creation processes and requirements for applicants and beneficiaries to prove their identities can shape who has access to essential public benefits, and how quickly individuals can apply for and start receiving benefits. This research aims to build a comprehensive understanding of the digital identity landscape in public benefits and help stakeholders identify promising approaches as well as potential barriers to access.
The DBN will publish the fully updated dataset and accompanying analysis later this fall to help track where states have made changes to their application processes. Ahead of that, we want to highlight some of the new data points we’re capturing this year and offer a sneak peek of what we observed this summer.
New Data Points
In this update of our landscape dataset, we are excited to add new data points to our research, including:
- Information on portals’ password recovery mechanisms.
- Why it matters: If applicants/beneficiaries are unable to access self-service pathways to regain access to their account, this can drive up calls to call centers and prevent people from responding to important notices or requests for information.
- How applicants are directed to get help on the portal.
- Why it matters: Ideally, application processes are straightforward. But how applicants can access help and information (through things like FAQ pages, video tutorials, chatbots, etc.) matters for strong, equitable access.
- Whether applications ask applicants about their communication preferences.
- Why it matters: Reaching applicants via the medium they are most comfortable with or are most likely to have access to could help ensure eligible individuals complete application requirements and maintain benefits.
CX Challenges + Opportunities: Account Creation
As student analysts with the DBN, we’ve learned to think about the design of digital identity practices as a key part of customer experience (CX). We’ve been learning more about guidance coming from the f level to promote CX and digital services (for example the White House Executive Order on Customer Experience and guidance from federal initiatives and agencies, including USDOL Office of UI Modernization, HHS-Facing Financial Shocks, and USDA-FNS ) as well as state efforts. In summer 2024, the DBN also hosted a series of CX webinars, which gave us another opportunity to deepen our understanding of this topic.
As we went through and updated the DBN’s Digital Identity Dataset this summer, we reviewed dozens of online benefits applications. We had extensive time and resources to review applications, but still encountered challenges interacting with different systems. We were especially interested in some of what we observed related to the CX of account creation and starting applications.
Once we were able to locate an online application for a given program in a particular state, it wasn’t always clear how to access the application or get started. Many applications required account creation, and those registration processes varied significantly in terms of complexity. Some require email addresses, others are integrated with state single sign-ons (SSO), or ask people to use their Facebook or Gmail credentials to login. Some applications did not have an account creation process, while others offered a guest flow where applicants had access to limited features.
As the DBN has previously written, state agencies should evaluate when account creation is necessary for security goals, and make guest application pathways available. For applications that did require accounts, once we were able to start account creation, we observed key challenges related to account protections and multi-factor authentication (MFA), including:
- Security questions that were very restrictive, e.g., requiring minimum six character answers.
- Wide variation in how many security questions users could choose from, like ones that didn’t offer enough choice (only one question) to those that offered too much choice (53 unique questions).
- Security questions that were not trauma-informed (e.g., asking users to recall where they were on September 11th, 2001).
- Password requirements that were cumbersome (e.g., requiring users change passwords periodically)
- Applications that assigned numbers that users need to keep track of to re-access a portal.
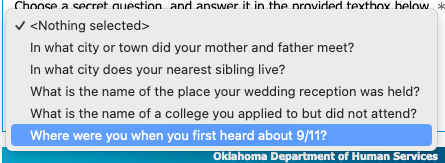
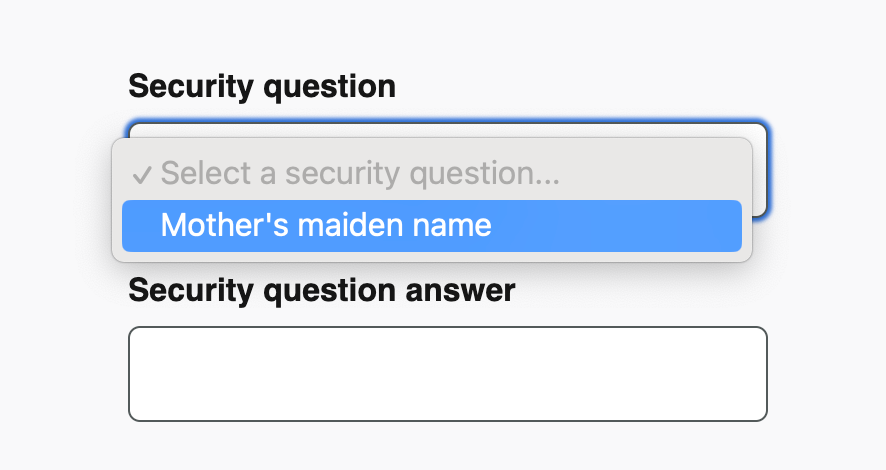
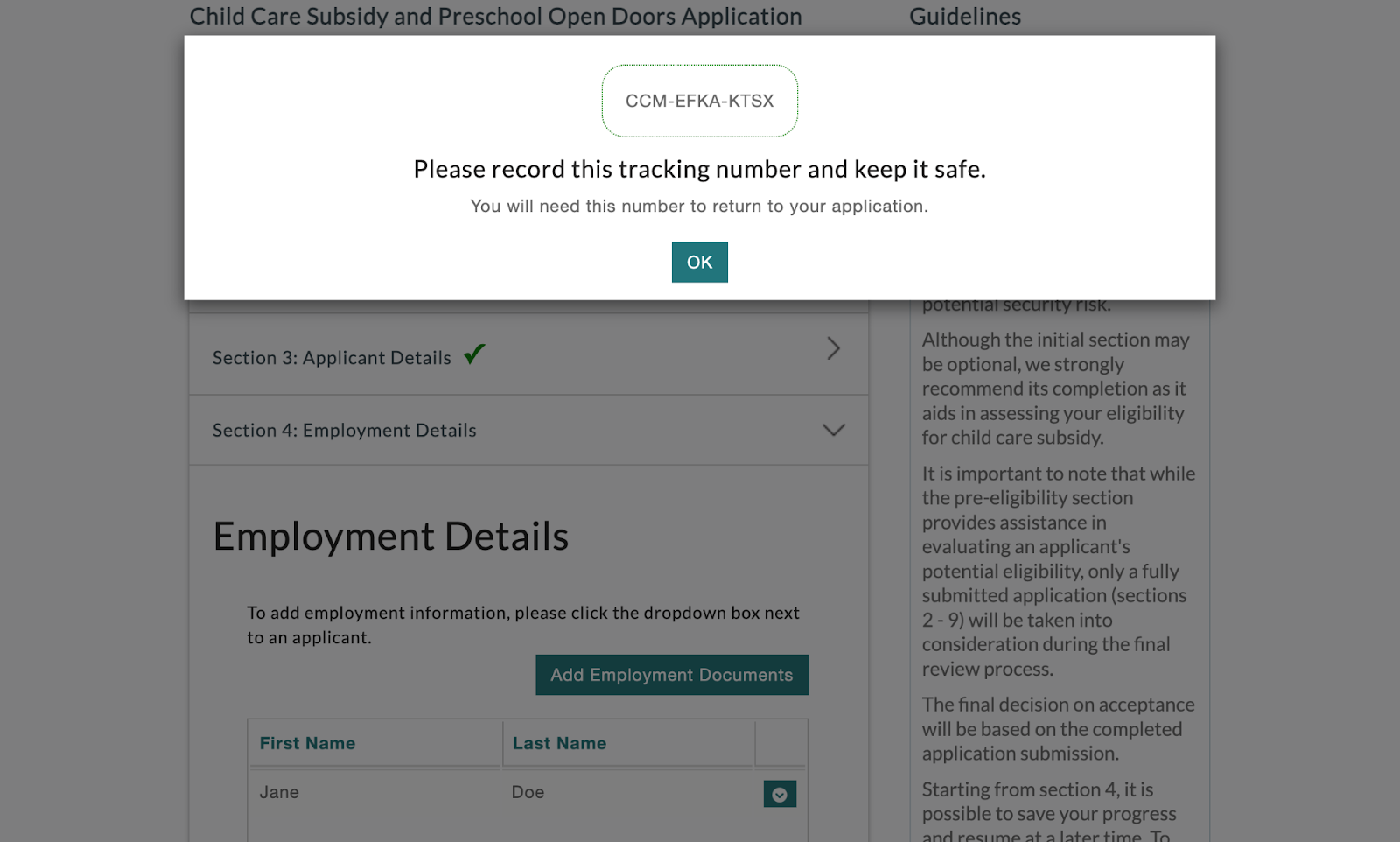
It’s important to note that due to their high risk for data breaches, phishing, and hacks, the National Institute of Standards and Technology (NIST), which issues digital identity guidelines, does not consider security questions to be an acceptable authentication method. Platforms using security questions should consider using other MFA options, but at minimum ensure that questions are confidential (e.g., a hacker couldn’t find out this information by looking through your Instagram account); memorable (i.e., something you can immediately recall); consistent (i.e., your answer won’t change over time); simple; and have multiple options to choose from.
While other types of MFA may be more secure compared to security questions, they can still be vulnerable. If a state believes account creation is necessary for a particular use case, they should reference NIST’s guidelines to consider phishing-resistant MFA and pay careful attention to how implementing MFA could affect users—especially those with limited device access, or who share devices—and implement MFA in ways that offer users flexibility.
We also encountered examples of security practices that felt more user-friendly:
- Applications that let users skip account creation when applying and create an account later;
- MFA that provided users with flexible options, such as allowing users to set up multiple preferences for MFA that made the process more flexible; and
- Password creation/entry fields that let us see what we were typing and clearly showed all password requirements.
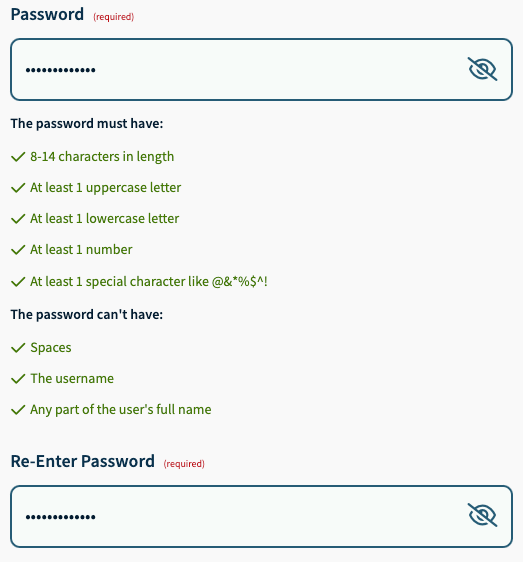
Conclusion
Later this fall, the DBN will publish a fully updated dataset with new analysis to help practitioners understand the digital identity landscape in public benefits applications in 2024. Supporting practitioners in government to balance access, security, and privacy, is a key priority for the team and there are lots of other ways to stay engaged with us on this topic, including:
- Stay tuned for the launch of our new Digital Identity Community of Practice. The DBN is standing up a new community of practice to promote the delivery of public benefits to all eligible individuals, including vulnerable populations, by informing how digital identity approaches should be used in public benefits delivery.
- Engage in our collaborative research project with NIST and CDT. The DBN is working with the National Institute of Standards and Technology and the Center for Democracy and Technology to develop resources that empower state benefits administering agencies to evaluate whether and at what level authentication and identity proofing are needed for specific benefits delivery scenarios. Sign up to receive more information and updates.
- Reach out if you have questions. We’re always excited to speak with practitioners working to improve digital delivery of public benefits. Email us at digID@georgetown.edu with questions or ideas.